SMUCSE 5349/73491 Authentication Protocols. SMUCSE 5349/73492 The Premise How do we use perfect cryptographic mechanisms (signatures, public-key and symmetric. - ppt download

CryptographyBhutan - Lesson 12 #securitymechanism #securityservices Security services are implemented by a security mechanism or combination of mechanisms: 1. Peer entity authentication service can be implemented by or combination of Encipherment, Digital

Adaptive Security in Dynamic Group Communications: Dynamics-aware key management and data origin authentication techniques for highly dynamic and large scale multi-party communications: 9783639203745: Computer Science Books @ Amazon.com
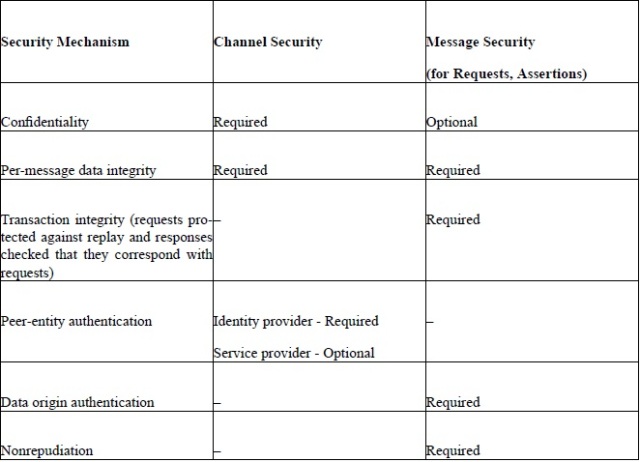
General Security and Privacy Mechanisms for Liberty Identity Web Services Framework | Protogenist Blog




![MS-AUTHSOD]: Data Origin Authentication (Signing) | Microsoft Learn MS-AUTHSOD]: Data Origin Authentication (Signing) | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-authsod/ms-authsod_files/image027.png)